siem slam: tricking modern SIEMs with fake logs & confusing blue teams
in this post, I will basically outline my latest research and provide some links for further details.
if you want to learn more about it/contribute, you are always more than welcome to reach me.
quick note: it’s been almost a year since the first time I started working on that research. I am still working on it and things are getting naughtier than what I told you before 👀

abstract
every company undoubtedly trusts its SIEM, right? Think twice, we can inject fake logs, distract BT’s and hide our attacks.
it is even possible to inject logs from future and past, we called it Time Traveller’s attack. This research covers different ways to exploit this weaknesses, teach blueteams to be careful about this attack and possible mitigations/hardenings.
what we did
default SIEM configurations have some weaknesses, and there is no just one robust way to prevent it in huge environments. in our research, we intercepted and examined the traffic between Splunk’s internal components and noticed that we can actually modify it.
to illustrate these vulnerabilities, we developed log-slapper a tool designed for the offensive security community to enhance red team operations following successful inital compromise.
examining Splunk structure
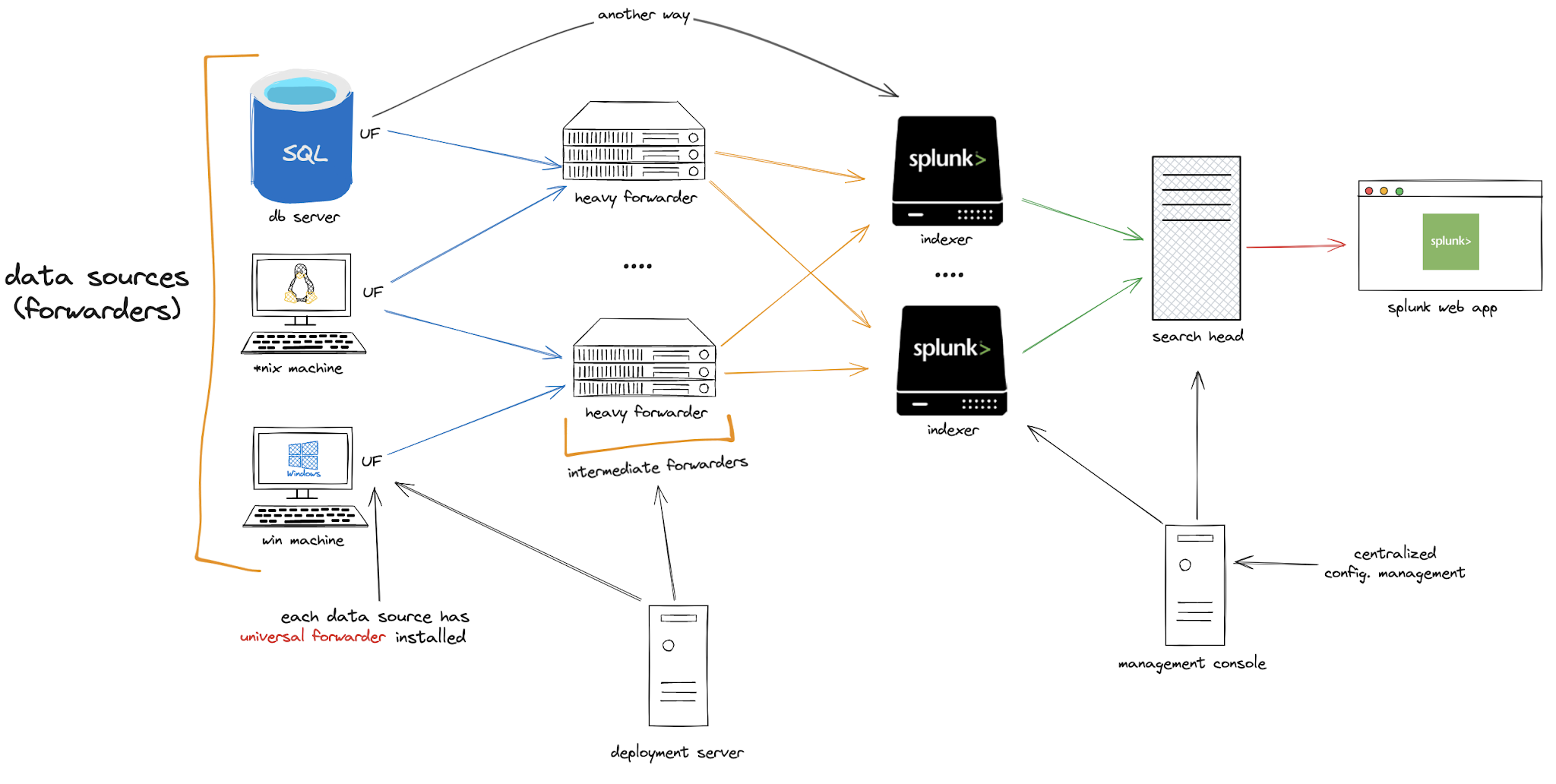
our main point of focus in that structure is the communication between UFs and HFs (or Indexers)
UF: it is basically an agent you deploy on IT systems, which collects logs and sends them to the indexer/hfs.
HF: unlike UF, it parses the data before forwarding to the indexer
Indexer: it indexes data and transforms upcoming raw data to the readable events, a form that is searchable
what hacker really needs

after an initial compromise, we need some time for:
- exfiltrate data
- lateral movement
- find hidden gems across the network
what can attacker do?

yep, you heard it right. we can indeed inject logs. by doing that, we also can:
- mimic another attack
- spam logs
- basically, make fkin chaos
log-slapper:
here is the tool, feel free to use, contribute and test your environment!
further details:
I will continue to give details about the research and enrich this blog post. But for now, you can watch my latest talk: